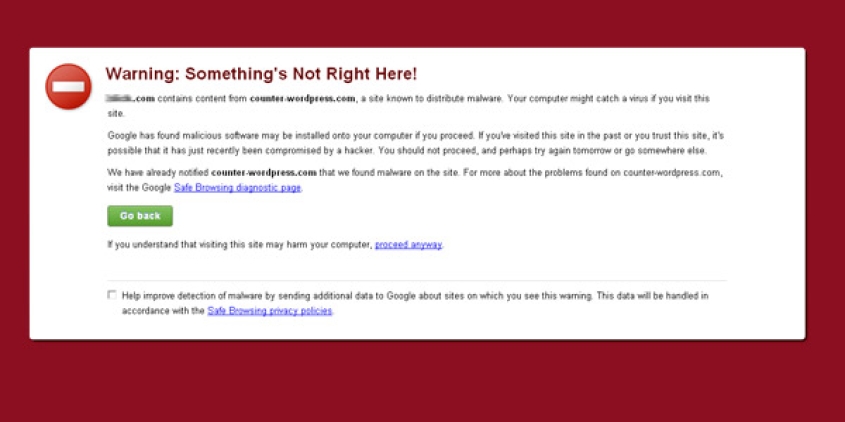
If you've gone to your WrodPress website, in the Chrome browser and have seen this message:
Warning: Something's Not Right Here!
contains content from counter-wordpress.com, a site known to distribute malware. Your computer might catch a virus if you visit this site...
Then your WordPress website has most likely fell victim to a hacker exploiting the vulnerability in your Timthumb.php file. The truth is, there's no telling what someone can do once they're able to get into your website like this. There is trend in what scripts are hacked and they can sometimes be easily fixed.
Timthumb.php Vulnerability Common Fixes
First we'll update your timthumb.php file so that this vulnerability is gone.
Use an FTP program to replace your vulnerable timthumb.php file code with this newer version (Back up your original timthumb.php code before updating it just incase the new version brakes your site): timthumb.php zipped
Next we're going to clean out the most common infected files for this type of exploit. These files are the ones in your 'script' directory of the custom WordPress theme and your config.php file in the root of your install. Here's some instructions on how to replace the files:
- Connect to your website via FTP
- Unzip the custom WordPress theme, that you used for your WordPress website, into a directory on your computer.
- Download the 'scripts' from your WordPress website: 'wp-content\themes\yourthemefolder\scripts' then delete the 'scripts' folder on your server.
- Upload the scripts folder that you just unzipped from your theme into the 'wp-content\themes\yourthemefolder\' on your server. Now most of the hacked files should be replaces.
- Download the 'wp-config.php' from the root directory of your WordPress install. Open this file in notepad or a code editor. This file should be about ~90 lines long. If your file is much longer then this and or has extremely large blank spots in the code (over 30 lines long) it's probably been tampered with.
So an infected wp-config.php file will have about ~90 lines or proper code, a ton of blank lings, a bunch of lines of hacking code, a ton of blank lines again then the end of the document. Back this hacked file up as wp-config_hacked.php and create a duplicate of it. - Highlight the blank lines of code, the hacking code that's between them and delete it all.
- Save this file as wp-config.php
- Upload your new wp-config.php into the root directory of your WordPress install replacing the current one that's there.



Before you post, please prove you are sentient.
Wait! The answer you gave wasn't the one we were looking for. Try another.
What is frozen water?